GAO Wants Time Frames to Complete DHS Efforts on Critical Infrastructure Security

Protecting critical infrastructure—like water supplies, electricity grids, and food production—is a national priority. Events like natural disasters or cyberattacks can disrupt services that Americans need for daily life.
Many federal agencies are tasked with protecting the nation's critical infrastructure and look to the Cybersecurity and Infrastructure Security Agency for leadership on how to do it.
A 2021 law expanded these agencies' responsibilities and added some new ones. CISA is working on guidance and more to help agencies implement these responsibilities. We recommended that CISA set timelines for completing this work.
GAO found that the William M. (Mac) Thornberry National Defense Authorization Act for Fiscal Year 2021 expanded and added responsibilities for sector risk management agencies. These agencies engage with their public and private sector partners to promote security and resilience within their designated critical infrastructure sectors. Some officials from these agencies described new activities to address the responsibilities set forth in the act, and many reported having already conducted related activities. For example, the act added risk assessment and emergency preparedness as responsibilities not previously included in a key directive for sector risk management agencies. New activities officials described to address these responsibilities included developing a risk analysis capability and updating emergency preparedness products.
The Department of Homeland Security's (DHS) Cybersecurity and Infrastructure Security Agency (CISA) has identified and undertaken efforts to help sector risk management agencies implement their statutory responsibilities. For example, CISA officials stated they are updating key guidance documents, including the 2013 National Infrastructure Protection Plan and templates for revising sector-specific guidance documents. CISA officials also described efforts underway to improve coordination with sector partners, such as reconvening a leadership council. Sector risk management agency officials for a majority of critical infrastructure sectors reported that additional guidance and improved coordination from CISA would help them implement their statutory responsibilities. However, CISA has not developed milestones and timelines to complete its efforts. Establishing milestones and timelines would help ensure CISA does so in a timely manner.
Why GAO Did This Study
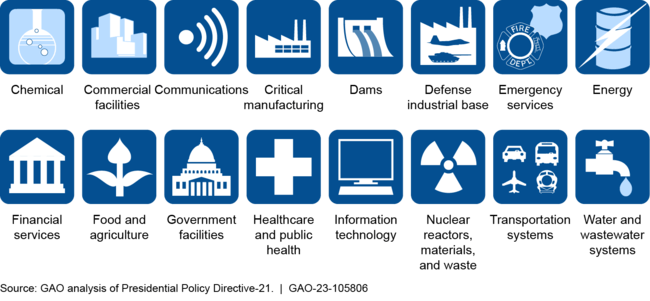
Critical infrastructure provides essential functions––such as supplying water, generating energy, and producing food––that underpin American society. Disruption or destruction of the nation's critical infrastructure could have debilitating effects. CISA is the national coordinator for infrastructure protection.
The William M. (Mac) Thornberry National Defense Authorization Act for Fiscal Year 2021 includes a provision for GAO to report on the effectiveness of sector risk management agencies in carrying out responsibilities set forth in the act. This report addresses (1) how the act changed agencies' responsibilities, and the actions agencies have reported taking to address them; and (2) the extent to which CISA has identified and undertaken efforts to help agencies implement their responsibilities set forth in the act.
GAO analyzed the act and relevant policy directives, collected written responses from all 16 sectors using a standardized information collection tool, reviewed other DHS documents, and interviewed CISA officials.
Recommendations
The Director of CISA should establish milestones and timelines to complete its efforts to help sector risk management agencies carry out their responsibilities. DHS concurred with the recommendation. Additionally, GAO has made over 80 recommendations which, when fully implemented, could help agencies address their statutory responsibilities.
Recommendations for Executive Action
Agency Affected
Cybersecurity and Infrastructure Security Agency
Recommendation
The Director of CISA should establish milestones and timelines for its efforts to provide guidance and improve coordination and information sharing that would help SRMAs implement their FY21 NDAA responsibilities, and ensure the milestones and timelines are updated through completion. (Recommendation 1)
Actions to satisfy the intent of the recommendation have not been taken or are being planned.