TSA leaders share tips to get through airport security during the pandemic

There are a handful of actions that travelers can take in an effort to get through Transportation Security Administration (TSA) airport checkpoints during the pandemic in ways that may help reduce the likelihood of contracting COVID-19.
While security is TSA’s top priority, the health and safety of TSA employees and the traveling public is of utmost importance. TSA remains in close communication with medical professionals, the CDC, and various government agencies as we continue to carry out its security mission during the pandemic.
Here are a few suggestions that TSA Federal Security Directors want to share with travelers who are scheduled to fly during the pandemic.
- John Bambury, TSA Federal Security Director for John F. Kennedy International Airport: “You’ve heard it a thousand times—wear a mask. I wear a mask every single day at the airport, which is one of the top recommendations from the CDC. If you’re flying, you should also consider carrying an extra mask so that if the elastic band snaps on your mask, you’ve got a spare one handy. Also, you may want to change into a fresh mask upon arrival at your destination. If you don’t have a mask, the TSA officer at the travel document checking podium will offer you one for free. When you get to the travel document podium, the TSA officer will ask you to remove your mask for just a few seconds to verify that your face matches the ID that you are presenting.”
- Scott T. Johnson, TSA Federal Security Director for Washington Dulles International and Ronald Reagan Washington National Airports: “Consider enrolling in TSA PreCheck® because it gets you through the checkpoint conveniently and more quickly than a standard checkpoint lane, making it even more valuable in today’s travel climate. TSA PreCheck passengers spend less time waiting in line and keep their shoes, belts and jackets on during screening and electronics in their carry-ons, reducing overall contact during screening. Travelers in the program also are permitted to leave their 3-1-1 liquids bag in their carry-on bags.”
- Gerardo Spero, TSA Federal Security Director for Philadelphia International Airport: “Know before you go. By that I mean that you need to know what is in your carry-on bag before you head to the airport to ensure that you have nothing prohibited with you. Prohibited items such as large liquids, knives, pepper spray, loose ammunition, and other prohibited items result in our need to open your carry-on bag and remove them. This keeps you in the checkpoint for an extra few minutes while one of our TSA officers opens your carry-on to search and eventually remove the item. We want to get you through the security checkpoint efficiently and quickly. Prohibited items slow you down.”
- Thomas Carter, TSA Federal Security Director for Newark Liberty International Airport: “The CDC recommends washing your hands frequently. Consider washing your hands before and after completing the security screening process. If it is not possible to wash your hands, please use hand sanitizer. TSA has instituted a temporary exemption from the 3-1-1 rule, that permits travelers to carry up to one 12-ounce container of liquid hand sanitizer per passenger, in carry-on bags. You can also bring individual hand wipes or a large tub of hand wipes with you to help wipe down your hands and even handles of your carry-on bags.”
- John C. Allen, TSA Federal Security Director for Yeager Airport: “Do your best to socially distance from others whenever possible. By that I mean, leave some extra space between the traveler in line ahead of you. Take that an extra step back. After you go through the checkpoint scanner, that’s another opportunity to take an extra step back while you wait for your carry-on items along the conveyor belt. Look around, see where you can wait for your carry-on items a little farther away from fellow passengers. Then take your belongings off to the side to put on your shoes, jacket and other items so that you’ve got some extra space of your own to recompose.”
- Grant Goodlett, TSA Federal Security director for Baltimore/Washington International-Thurgood Marshall Airport: “If you haven’t traveled in a while, you will notice that TSA has installed acrylic shields in checkpoints in an effort to make the screening process safer for passengers and our workforce by reducing the potential of exposure to the coronavirus. Please don’t walk around these acrylic shields to interact with our TSA officers. The shields have small vents to allow for conversation, questions and answers to be shared.”
[Source: TSA]



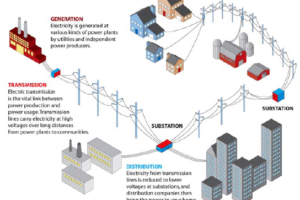
 A stable homeland is dependent on the reliable delivery of electricity—from public health to the economy and national security. According to DOE's Grid Modernization and the Smart Grid project, there are more than 9,200 electric generating units with more than 1 million megawatts of generating capacity feeding more than 600,000 miles of transmission lines that comprise the U.S. electric grid.
A stable homeland is dependent on the reliable delivery of electricity—from public health to the economy and national security. According to DOE's Grid Modernization and the Smart Grid project, there are more than 9,200 electric generating units with more than 1 million megawatts of generating capacity feeding more than 600,000 miles of transmission lines that comprise the U.S. electric grid.