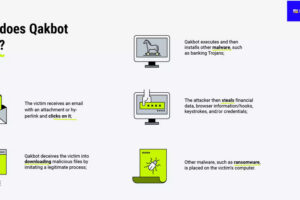
Sarah-Jane Prew, a security consultant from Arup, discusses the unique security challenges presented by sites that are both Critical National Infrastructure (CNI) and Publicly Accessible Locations (PALs) and offers some insight into how the sometimes opposing priorities can be managed.
Protecting Critical National Infrastructure (CNI) sites is a large part of the security profession’s role; preventing hostile intervention while assuring resilience to ensure that the sec-tor can keep the nation’s critical services operational. As the name suggests, CNI is about critical services and infrastructure and therefore security is usually associated with protecting assets and information by keeping unauthorised people out.
However, what if that CNI site is also a Publicly Accessible Location (PAL) and exists for the very function of allowing people in? How do you maintain and protect the criticality of the asset and function while not being able to keep people out? And how do you deal with the fact that the presence of all those people creates a target in itself, and thus an additional type of threat, one that aims to kill and injure crowds of people but in doing so, disrupts the very CNI function you were originally trying to protect?
Two CNI sectors typically fall into this category by definition …. transport and health. An airport and a hospital, for example, exist for the very purpose of ‘allowing people in’ and yet are often defined as CNI due to their resilience and criticality, therefore requiring the levels of security afforded by their status. Increasingly, other sectors are also opening up their facilities electively to the public - many offering public realm areas in their offices where people can enter freely and enjoy a coffee while others combine the occupation of CNI sites with other, less or non-critical, industries.
In these cases there needs to be a successful blend between protecting both the CNI and PALs elements but often the lines between then are confused. Whereas in the protection of CNI the primary focus is on the protection of the asset and function, in a PAL the focus is on protecting crowds of people. This relatively obvious statement, however, often leads to counter-intuitive responses in the implementation of security processes.
Typically this is seen where screening is placed further and further out, away from the core of an asset. In airports, for example, and often in publicly accessible government buildings, it is common to see screening just inside the doorway or even outside. What is this security design aiming to achieve?
The introduction of this additional screening is often implemented post an incident, such as an explosive device detonating in the check-in area of an airport. The instinctive reaction is to try to prevent that from happening again. Screening before entry to the building will minimise the chances of that happening in the same place again. But will it minimise the chances of it happening elsewhere at the same site? No … if anything it offers the attack-er a more convenient solution and a more accessible target …. a queue outside a building, close to a glazed facade or entrance.
So what, in this instance, is the security policy trying to protect? If it is the asset then the policy may be on the correct lines …. but if it is the crowds of people that frequent the site then they are just moving the threat elsewhere and arguably making the new target an easier and more attractive one. Needless-to-say, whether the target is CNI or people, the ultimate result is the same - a loss of function ….. only the number of casualties varies with the addition of loss of life in the latter case.
Experience has taught us, in both the Manchester Arena incident and in the Paris Stade de France attacks that terrorists, even suicide bombers, can be easily deterred from pushing through security lines into the hearts of sites but will instead maximise the easier opportunities outside the perimeter, even if less crowded, to attack.
So why are we still seeing poor security design in so many of these sites? Is it just a lack of thought process or an unclear view of what to protect? Is it that the vulnerabilities are not sufficiently risk assessed so there is a lack of clear focus on where to concentrate re-source? Or is there sometimes a more complex issue that has something to do with conflicting priorities? This can certainly happen sometimes if the sector is in a regulated space.
Aviation, for example, a sector that has been overseen by regulation since its conception, often struggles to have a clear ability to focus on the broad range of threats now facing it because the regulators’ focus still tends to be very narrow - protecting the aircraft and the parts of the airport that are essential to ensuring this protection. Aviation security regulation is complex and often slow to respond to changes in threat profile. This is especially evident in those soft target, landside, publicly accessible parts of the airport which are essentially non-regulated spaces.
Adding to this, there is a dichotomy around regulation and the acceptance of anything beyond its requirements on the part of sites; while regulation enforces a standard of protection, even accepting that it usually plays to the lowest common denominator of those who have to abide by it, it can be doubly challenging, in a regulated space, to gain engagement with and funding for the implementation of concepts that are beyond minimum requirements.
Commerciality is another major factor that affects security decisions more often than is helpful when aiming to protect both CNI and PALs concurrently. Even where public access is inevitable, such as an airport or railway station, the fashion in some parts of the world is to maximise the public access throughout the site, in an effort to increase commercial re-turn.
Large scale airport cities, for example, where people visit for the experience itself - be-cause the site contains shopping malls with dining opportunities, integrated hotels, swimming pools, cinemas and even event spaces, are becoming increasingly popular - at a time when attacks on airports in recent years have been numerous and on crowds of people even more so.
An attack on crowds of people could happen anywhere, of course, but what architects and designers often forget is that if that attack happens within a CNI site, even if it is not targeting the site itself but the people who have congregated there, the incident does not just close down the shopping mall or the cinema where the attack happened …. it shuts down the entire CNI asset that surrounds it. This is especially so in aviation because it is the larger, more significant airports - the ones more likely to be designated CNI - that tend to be the ones following this trend and offering more in the way of public amenities.
While the problem of combining CNI sites with PALs is challenging enough and the development of commercial ventures within CNI sites increases the associated problems, is-sues are compounded further when little thought is given to the security of the design of such developments because these are the exact areas of the site, especially in airports and railway stations, that are not necessarily considered under transport security regulations. This leaves security managers under pressure to develop and implement security regimes whilst enabling revenue-generating commercial activities.
Managing security design within CNI where large crowds of people are present clearly presents significant challenges. When the challenge is multi-faceted, an equally multi-faceted approach needs to be adopted to achieve the best chances of success. This involves taking a risk-based approach while working alongside a number of agencies and understanding the full range of threats and their inter-operabilities so a layered and intelligent process of security can be adopted.
The first step is to assess the risk to the site, from both the perspective of the site being CNI and a Publicly Accessible Location. Assessments need to be made as to the safety and security priorities and what measures need to be implemented to protect which as-sets.
From a design perspective, it is essential that security professionals are involved in any design projects from the start to undertake these risk assessments early enough in the process that the design itself can ‘design out risk’, therefore reducing the number of security features that need to be added to minimise the risk and mitigate the effects of an at-tack. As well as providing the most robust security in the most aesthetically pleasing way, this is also the most cost and time effective way of ensuring good security.
Without early intervention and assessment of the whole site, security can be compromised due to prioritising the protection of one element over another, rather than addressing the site holistically. This will lead to push-back on developing further security due to lack of space, resource or time.
Take the example of positioning security screening further out to protect an inner asset …. This succeeds in reducing the risk to the inner asset but actually increases the risk to the individuals queuing to be screened by making them an easier target. If the two problems are not addressed together, then one will inevitably lose out, as the design of one in isolation is likely to compromise the security of the other.
While embedding security in the design is essential, it can’t achieve everything and it is important to consider operational factors, especially for sites that attract large numbers of people. It is vital that all stakeholders are involved in security developments to ensure that their requirements are met and their operational needs incorporated. It is also essential that the multi-agency approach is adopted, which ensures that all those involved in man-aging security operations are brought together to ensure a fully co-ordinated strategy in terms of protection, detection, response, resilience and, if things do go wrong, recovery and business continuity.
Beyond the physical measures it is important to move the security perimeter out so there is vigilance far beyond the immediate vicinity of what you are aiming to protect, particularly when this is groups of people. For example, it is too late, at a screening point, to develop a suspicion about someone who may be targeting the crowds in that screening queue. By pushing the perimeter of surveillance out beyond this, operators can monitor the demo-graphic and behaviour of those approaching, giving time for an intervention if required.
In a time when pressure is on sites to reduce operational costs, this level of security operation is often met with reluctance but complex security needs require layers of mitigation and this requires both physical and operational measures.
Ultimately, those areas that are not currently governed under regulation, especially when situated within sites that have areas and operations that are under a regulatory frame-work, would merit from having more published guidance. This would ideally show clear areas of responsibility so organisations can assess their risks and priorities holistically, across the whole site, according to the risk presented, rather than a bias of focus and re-source from having regulatory requirements in one place and a lack of them in another.
The above considerations will give some solutions to the challenge of protecting those CNI sites that are also Publicly Accessible Locations (PALs); a question that is going to continue to face the security industry as more CNI sites are allowing the public into their sites.